Have you ever wondered how cybersecurity experts decide which threats to prioritize? Enter the Pyramid of Pain – a practical framework that helps you understand which security measures will cause the most trouble for attackers.
This easy-to-understand model shows exactly which detection methods will give you the biggest security bang for your buck. Created by David Bianco, the Pyramid of Pain helps security teams focus their efforts where they’ll be most effective rather than chasing every possible threat indicator.
What Is the Pyramid of Pain?
Think of the Pyramid of Pain as a way to rank the different clues (called indicators of compromise or IOCs) that tell you someone is attacking your systems. The ranking is based on how much trouble – or “pain” – attackers feel when you detect and block these indicators.
Here’s the key insight: when you focus on the higher levels of the pyramid, you force attackers to work much harder or even give up entirely. It’s like the difference between locking your front door (which is easy for a burglar to deal with) versus installing a complete home security system (which might make them target an easier house instead).
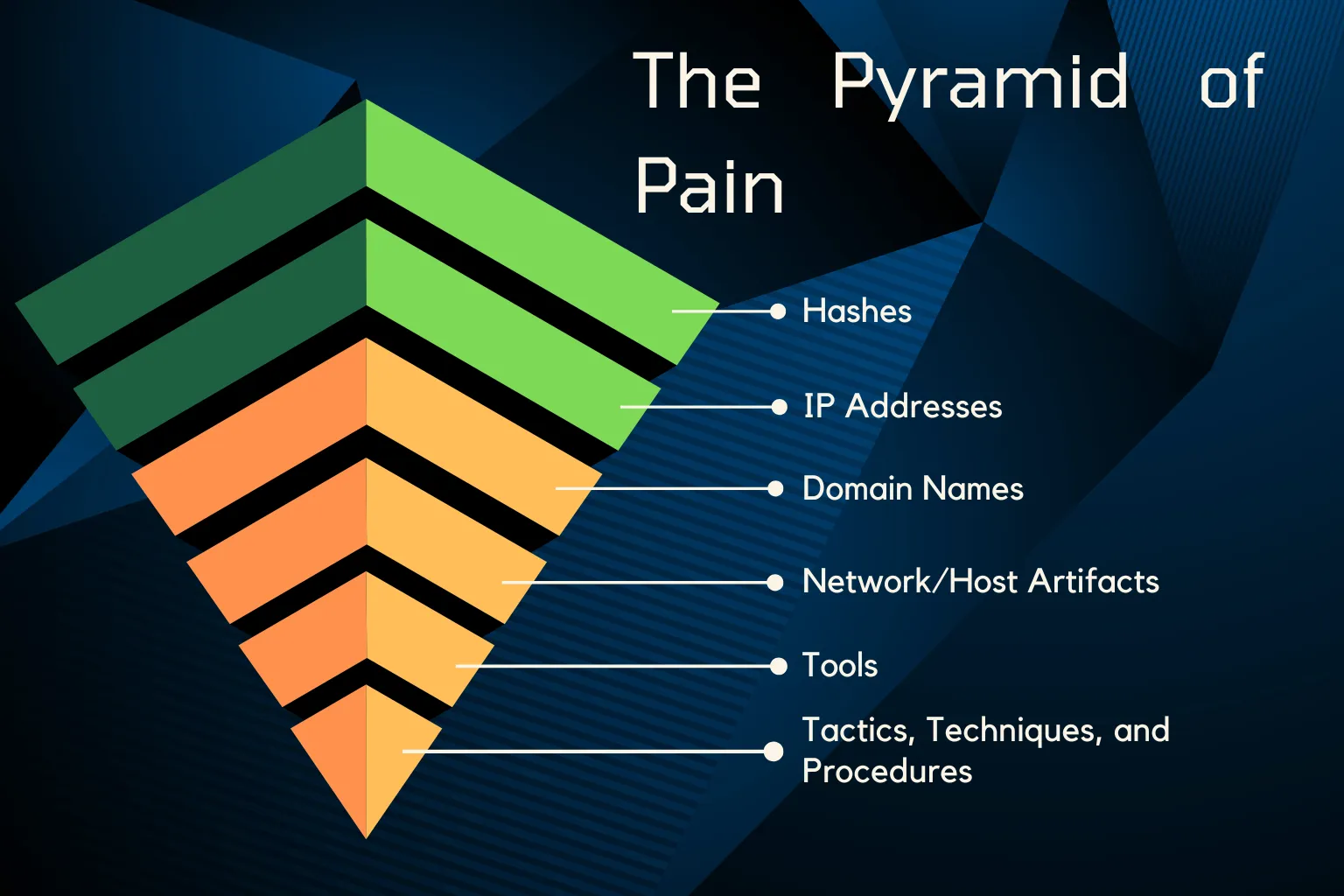
The pyramid has six levels, starting from the bottom and moving up:
- Hash Values (Trivial) – Easiest for attackers to change
- IP Addresses (Easy) – Simple to switch
- Domain Names (Simple) – Not too difficult to replace
- Network/Host Artifacts (Moderate) – Requires some effort to modify
- Tools (Challenging) – Requires significant work to alter
- Tactics, Techniques, and Procedures (TTPs) (Difficult) – Extremely hard to change
Let’s examine each level in detail to understand its significance and how organizations can leverage this knowledge to strengthen their security posture.
Hash Values (Trivial) - The Foundation Level
At the bottom of the pyramid are hash values – those unique string identifiers like MD5, SHA-1, or SHA-256 that work like digital fingerprints for files. While they’re easy to share in threat reports, they’re also incredibly easy for attackers to change.
Why They’re Easy to Beat
All an attacker needs to do is make a tiny change to their malware – even altering a single character – and the hash completely changes. The malware still works exactly the same, but your security tools won’t recognize it anymore!
Real-World Example
Imagine your security tool blocks a ransomware file with the hash 8b88dd36cee24090a76d9e18cde611cc. The attacker simply makes a small tweak to their code, and now it has a completely different hash like 7a9d8ca69f114de6745248b07b65a726 – and it sails right past your defenses.
Still Useful, But Limited
Hash values do help identify known threats exactly and are great for sharing in threat intelligence. Just don’t rely on them as your only defense – smart attackers will always find ways around them.
IP Addresses (Easy) - The Second Level
Moving up one level, we find IP addresses linked to malicious activities. Blocking bad IP addresses can stop attacks temporarily, but attackers find them fairly easy to change.
How Attackers Get Around IP Blocks
Attackers have several tricks to bypass IP-based blocks:
- They switch to services that give them new IPs regularly
- They use hacked computers as middlemen
- They leverage cloud services where getting new IPs takes minutes
- They set up networks that constantly shuffle their addressing
Real-World Example
An attacker running a command server at 192.168.1.100 gets blocked. No problem – they just spin up a new server in AWS or Azure with a fresh IP address in minutes, and they’re back in business.
Still Worth Doing
Despite these limitations, tracking and blocking suspicious IPs is still valuable. IP reputation services help identify known bad addresses so you can block them before they cause harm.
Domain Names (Simple) - The Third Level
Domain names sit at the third level of the pyramid. Changing domains takes a bit more effort than changing IPs, but attackers can still register new domains quickly and cheaply.
Common Evasion Tactics
Attackers use several methods to get around domain blocking:
- They create algorithms that automatically generate thousands of random domain names
- They register look-alike domains (like “g00gle.com” instead of “google.com”)
- They hide behind legitimate services
- They compromise legitimate websites temporarily
Real-World Example
When “malicious-site.com” gets blocked, an attacker quickly registers “ma1icious-site.com” (note the number “1” instead of letter “l”) or simply adds a different extension like “malicious-site.net” and continues their campaign.
Proactive Defense
Monitoring for suspicious domain registration patterns can help you spot potential attack infrastructure before it’s even used. This gives you a head start in protecting your systems.
Network/Host Artifacts (Moderate) - The Fourth Level
At this level, we’re looking at more specific technical footprints that malware leaves on your systems and networks. These include unique URL patterns, special HTTP header configurations, registry keys, file paths, and system objects like mutex names.
Why They Matter
These artifacts tell you exactly how malware operates within your environment. When you detect these patterns, you’re not just finding individual instances of malware – you’re uncovering their methods.
Why They’re Harder to Change
For attackers to change these, they must modify their actual code and how their tools work – not just surface details like what server they use. This requires real programming effort and testing.
Real-World Example
Imagine malware that creates a specific registry key at “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SuspiciousService” to automatically start when your computer boots up. If your security tools detect this specific pattern, the attackers must rewrite their code to use a completely different method of persistence.
The Security Advantage
By looking for these types of indicators, you can still catch attackers even when they’ve changed their IP addresses and domain names. However, determined attackers with enough technical skill can still modify these with some effort.
Tools (Challenging) - The Fifth Level
Now we’re getting serious! This level focuses on the actual software tools attackers use – their custom malware, modified hacking utilities, or commercial penetration testing tools that they’ve repurposed.
The Big Challenge for Attackers
When you can detect their specific tools regardless of how they’re delivered or how they communicate, attackers face a major hurdle. They must either heavily modify their tools or build new ones from scratch – both requiring significant expertise, time, and resources.
Real-World Example
If your security team can reliably detect Cobalt Strike (a popular attack tool) based on how it behaves rather than just its basic indicators, attackers face a serious problem. They must either significantly rework their attack tools or completely switch to different ones – neither option is quick or easy.
Modern Protection
Today’s advanced security tools use behavioral detection to identify malicious software based on what it does rather than static properties like file sizes or names. This approach significantly raises the difficulty level for attackers.
TTPs (Difficult) - The Peak of the Pyramid
At the very top of the pyramid are Tactics, Techniques, and Procedures (TTPs) – the crown jewels of threat detection. These represent the overall patterns of how attackers operate rather than specific technical details of their tools.
The Ultimate Defense
When you can detect attackers based on their methodologies and behaviors, you’ve reached cybersecurity nirvana. At this level, you’re not just finding their tools – you’re recognizing their entire playbook.
Maximum Pain for Attackers
Changing TTPs is extremely painful for attackers because it requires them to:
- Completely rethink their attack strategies
- Learn entirely new skills and techniques
- Develop and test new operational methods
This process can take months and may require them to start from scratch – an expensive and frustrating ordeal.
Real-World Example
If your security team can detect attackers moving laterally through your network using Windows Management Instrumentation (WMI) techniques – regardless of what specific malware they’re using – the attackers must now develop entirely new methods for expanding their access. This might require extensive research, testing, and possibly abandoning techniques they’ve relied on for years.
The MITRE Connection
The MITRE ATT&CK framework works perfectly with the Pyramid of Pain by cataloging these TTPs in detail. This framework helps you understand and defend against specific attack methods rather than just looking for individual malicious files or connections.
How to Apply the Pyramid of Pain in Your Security Strategy
Now that you understand the pyramid, how do you actually use it? The key is to build defenses at every level but focus most of your resources on the higher tiers where you’ll cause attackers the most pain.
5 Ways to Implement the Pyramid of Pain
- Create Multi-Layer Detection Don’t just look for known bad files (hashes) – also watch for suspicious behaviors. When your security tools can detect the patterns of an attack rather than just specific files, attackers have a much harder time getting around your defenses.
- Use Smart Threat Intelligence Go beyond simple blocklists. Look for threat intelligence that explains the “how” and “why” behind attacks, not just the “what.” This context helps you spot new attacks that use similar methods.
- Invest in Better Tools Choose security tools that can detect suspicious behavior patterns, not just match known bad signatures. Modern solutions like EDR (Endpoint Detection and Response), UEBA (User and Entity Behavior Analytics), and network traffic analysis see attacks based on how they behave, not just what they look like.
- Build Skills, Not Just Systems The highest level of the pyramid requires human intelligence. Train your team to understand attack techniques so they can spot unusual activities that automated systems might miss.
- Join the Community Share what you learn with other security professionals and learn from them too. When everyone contributes knowledge about attack methods, the entire community becomes stronger against threats.
Modern Challenges: Beyond the Basic Pyramid
While the Pyramid of Pain gives us a solid foundation, today’s security environment presents some additional challenges worth considering:
Speed Matters
The time between detecting an attack and responding to it can make all the difference. Automated systems can block attacks at the lower levels of the pyramid before they even have a chance to advance to more sophisticated stages.
Balancing False Alarms
As you move up the pyramid, detection methods tend to trigger more false alarms. Finding the right balance between effective detection and manageable alert volumes is crucial. Implement good triage processes to handle potential false positives efficiently.
Attackers Evolve Too
As defenders get better at detecting TTPs, sophisticated attackers will continue to innovate. Stay vigilant and keep learning about new attack methods as they emerge.
New Work Environments
With cloud services and remote work becoming the norm, traditional network boundaries are disappearing. Modern security strategies need to adapt the Pyramid of Pain concept to environments where the old idea of a secure perimeter no longer applies.
Conclusion: Making the Pyramid Work for You
The Pyramid of Pain isn’t just a nice theory – it’s a practical guide for deciding where to focus your security efforts when you can’t do everything at once.
By understanding which detection methods cause attackers the most trouble, you can make strategic decisions about where to invest your limited security resources. While you shouldn’t ignore the lower levels (hash values, IPs, and domains), the biggest security returns come from focusing on the higher levels – especially tools and TTPs.
When you detect and block attackers at these higher levels, you force them to work much harder and spend more resources to compromise your systems. This shifts the economics of cybersecurity in your favor, making attacks against your organization more costly and less attractive to potential adversaries.
The Pyramid of Pain helps you focus on what truly matters – disrupting attackers’ core operations rather than just playing whack-a-mole with easily changed indicators. In today’s complex threat landscape, this strategic approach is more valuable than ever.