How to Set Up IP Recon
First, I want to say thank you for downloading IP Recon. I hope this tool helps you create a safer internet.
After you download the application from the Windows app store, you will be prompted to enter an API Key. In order to user IP recon you need the following API key.
- AbuseIPDB: https://www.abuseipdb.com/register
- This API Key is free and provides 1000 look-ups a day.
Once the API key is entered, it is secured in your \AppData\Roaming\ folder as an encrypted file. You can read more about how your API key is encrypted at https://strombolisecurity.io/posts/ip-recon/. The key is locked to your machine and will only function on the host that created the key.
Didn’t Get IP Recon form the Windows App Store?
No problem! IP Recon is available for free at https://github.com/str0mboli/IPRecon. This version was built with python and work on Linux and MacOS. However, it does not have the UI features of the Windows App Store version. This getting started post is relevant to all version of IP Recon.
or
Get the latest version of IP Recon at: IP Recon Windows Store App
How to use IP Recon
IP recon is a straight forward application. Once the API key is secured, you can take any arbitrary text containing IP keys into the top left pane.
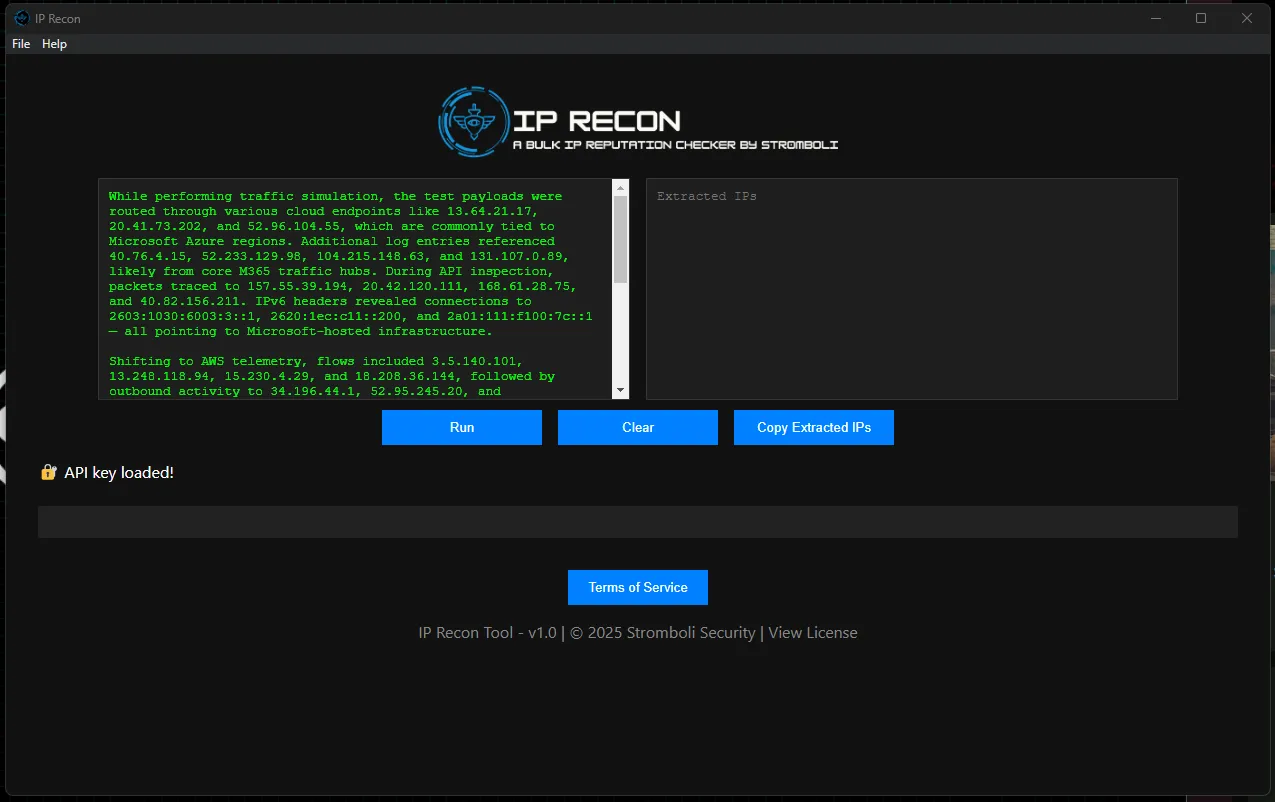
The application immediately extracts public IP and removes duplicate addresses and private network addresses.
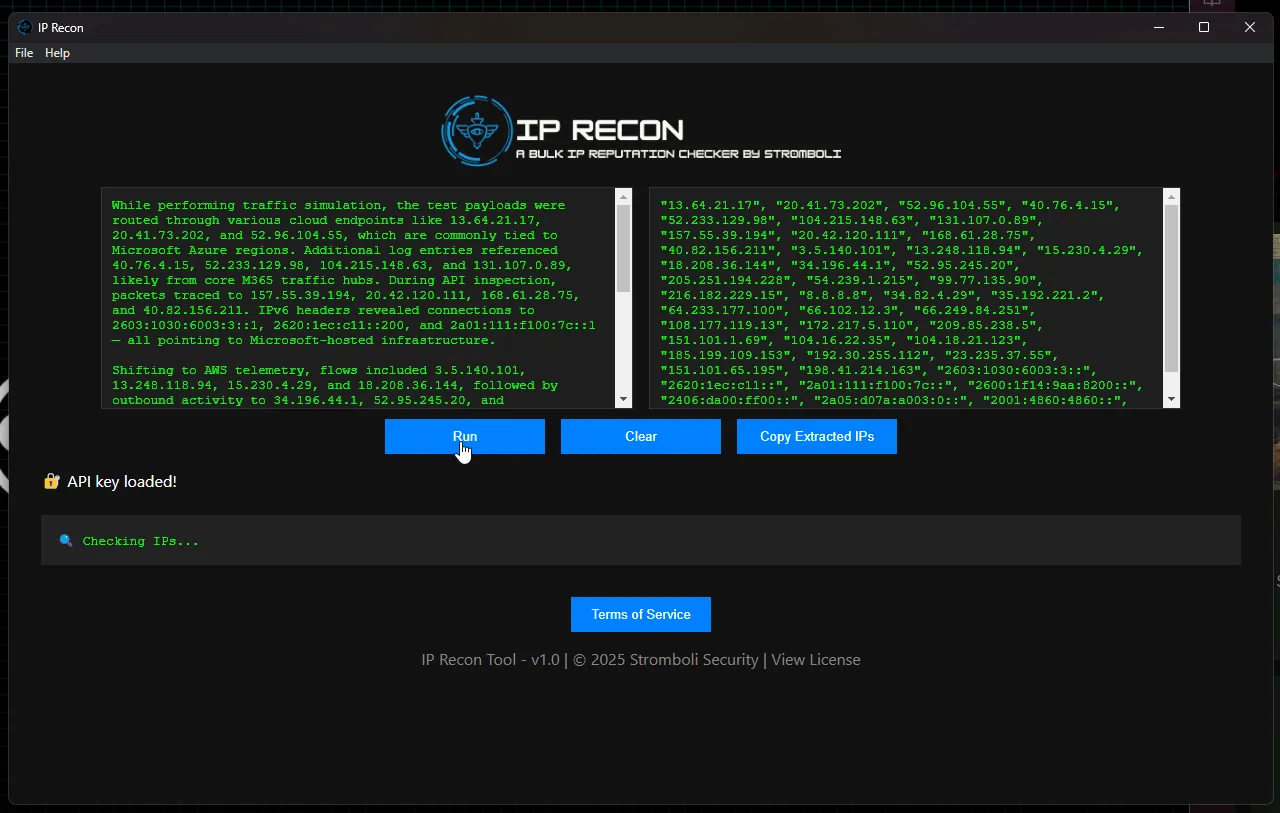
The format of the output is ready to be inserted into queries such as a KQL query to find out what sort of traffic an endpoint gnerated from these IPs.
Example KQL Query:
DeviceNetworkEvents
| search "TargetIP"or
// Define your list of IPs
let TargetIPs = dynamic(["13.64.21.17","20.41.73.202","52.96.104.55","40.76.4.15","8.8.8.8"]);
// Search the CommonSecurityLog table for any matching IPs in Source or Destination fields
CommonSecurityLog
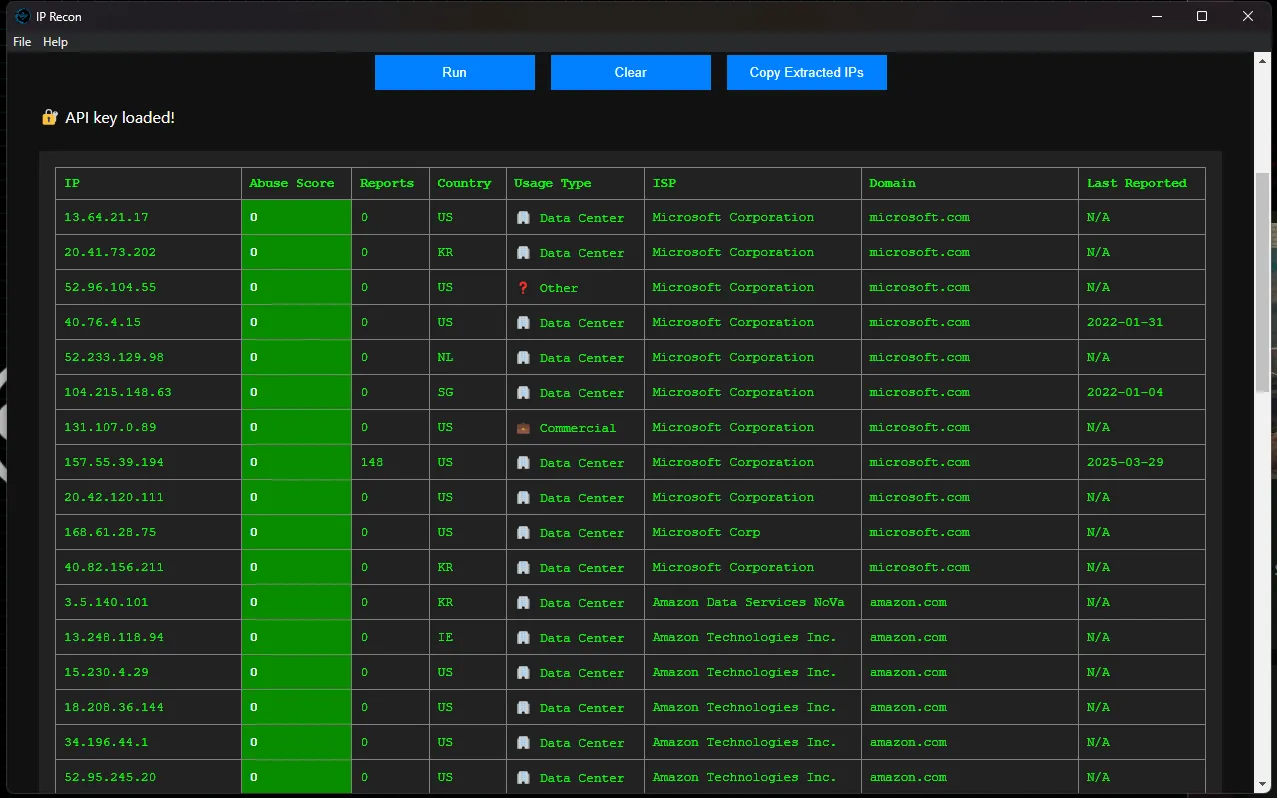
| where SourceIP in (TargetIPs) or DestinationIP in (TargetIPs)IP Recon sends these results to AbuseIPDB through the API call and returns the results in an easy-to-read table that is color coded based on abuse score. This allows you to quickly filter through large IP data sets and pinpoint potential malicious activity.
Results can be downloaded as a CSV file for easy inclusion in reports.
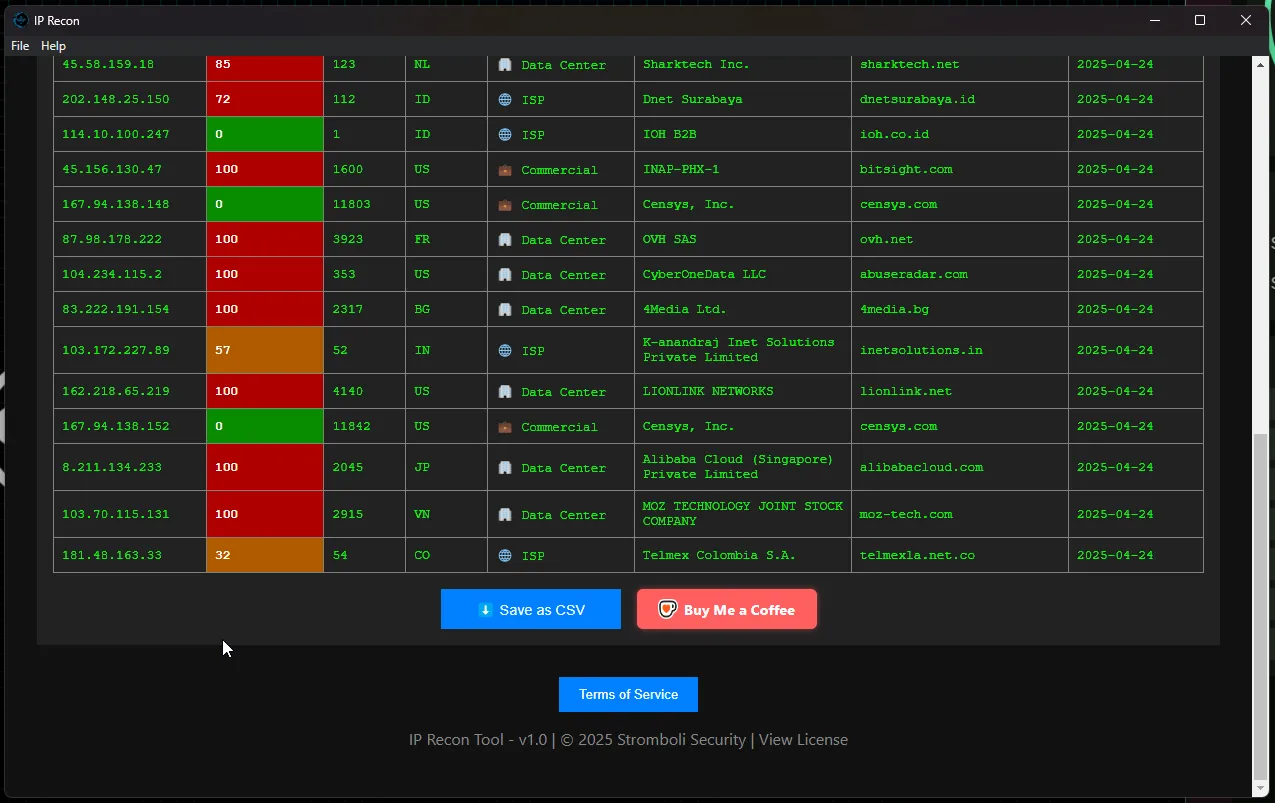
IP Recon is a free program, so donations are never required (but highly appreciated!).





