What is IP Recon
IP Recon is a security tool I developed to help me work security tickets that require reputation checks on a large number of IP addresses. I go by the name Stromboli. In real life, I work as a security analyst for an MSSP. For those who don’t know, an MSSP is a Managed Security Services Provider. We provide cybersecurity services for a wide range of businesses. On the job, there was no easy way to quickly parse and evaluate a large group of IP addresses for certain ticket types—so I made one.
IP Recon started as a Python project. The project is available on my GitHub. IP Recon is a GUI frontend that uses the AbuseIPDB API. It is a free, open-source program licensed under the MIT License. It is designed to run with a graphical interface for ease of use. It can even be compiled into a .exe file and run without the need for a terminal.
The current iteration is available in the Windows App Store. Screenshots in this post reflect the newer version, as the updated codebase allows for more customization and UI improvements.
Get the latest version of IP Recon at: IP Recon Windows Store App
What Does IP Recon Do?
IP Recon automates several repetitive data-parsing tasks and performs them in under 60 seconds.
The Use Case
You are a SOC analyst. You receive an alert for endpoints in your environment connecting to IP addresses listed in your threat intelligence watchlist. This is part of a daily scan, and typically these addresses are false positives. However, as you begin to review the list extracted from a CSV file, you notice some IPs you don’t recognize.
Example IP List from a CSV log
34.213.92.240 209.85.238.5 218.92.0.218 52.109.76.5 79.167.86.154 40.82.156.211 50.217.40.11 196.189.124.195 40.90.137.75 104.215.148.63 54.67.35.164 142.251.45.131 52.95.245.20 3.228.220.31 35.192.221.2 20.190.130.4 35.199.187.55 47.237.112.17 99.77.135.90 52.53.123.241 40.90.137.78 18.233.0.102 2001:4860:4860::8888 13.107.246.43 18.208.36.144 52.205.36.59 108.177.119.13 13.57.9.189 13.64.21.17 157.245.116.59 131.107.0.89 104.47.0.36 185.199.109.153 20.62.173.189 142.93.116.14 2a05:d07a:a003:0::fe 2406:da00:ff00::36 218.92.0.112 54.153.71.76 192.30.255.112 35.246.48.68 193.176.23.6 2620:1ec:c11::200 52.96.104.55 34.199.200.247 35.222.64.221 64.233.177.100 196.251.87.74 52.233.129.98 172.217.5.110 192.210.160.175 2404:6800:4003:c01::71 20.190.135.43 193.163.125.183 44.226.7.217 151.101.1.69 1.228.113.10 66.249.84.251 3.5.140.101 168.61.28.75 216.182.229.15 205.251.194.228 198.41.214.163 106.12.90.118 2a01:111:f100:7c::1 2600:1f14:9aa:8200::1 35.85.241.251 167.94.138.45 52.253.113.9 151.101.65.195 35.203.170.248 104.18.21.123 8.8.8.8 20.42.120.111 13.52.5.51 20.62.160.193 142.250.190.3 52.114.132.54 20.41.73.202 54.239.1.215 54.203.183.34 52.253.125.202 34.122.200.53 3.8.180.191 20.62.173.189 2607:f8b0:4005:80a::200e 23.96.52.53 3.230.93.188 40.76.4.15 66.102.12.3 104.16.22.35 40.90.137.76 34.230.61.101 13.107.6.254 34.82.4.29 209.85.238.5 52.108.0.0 34.68.194.64 104.47.51.36 157.55.39.194 23.235.37.55 104.215.148.63 52.109.88.13 52.173.6.212 2603:1030:6003:3::1 35.190.247.1 104.18.21.123 192.30.255.112 13.248.118.94 34.233.102.66 40.90.137.77 35.203.170.248 199.45.154.152 35.190.247.1 52.253.125.227 34.105.166.191 115.247.253.134 34.196.44.1 13.107.246.45 40.90.137.74 20.62.160.193 3.101.207.182 35.199.187.55 106.12.90.118 167.94.138.45 218.92.0.225
Luckily, you have IP Recon installed—so doing a reputation check on these IPs is no problem at all. After pasting your dataset into IP Recon, you run it and wait. Within a few seconds, IP Recon returns the results of its reputation lookup in a clean, easy-to-read table.
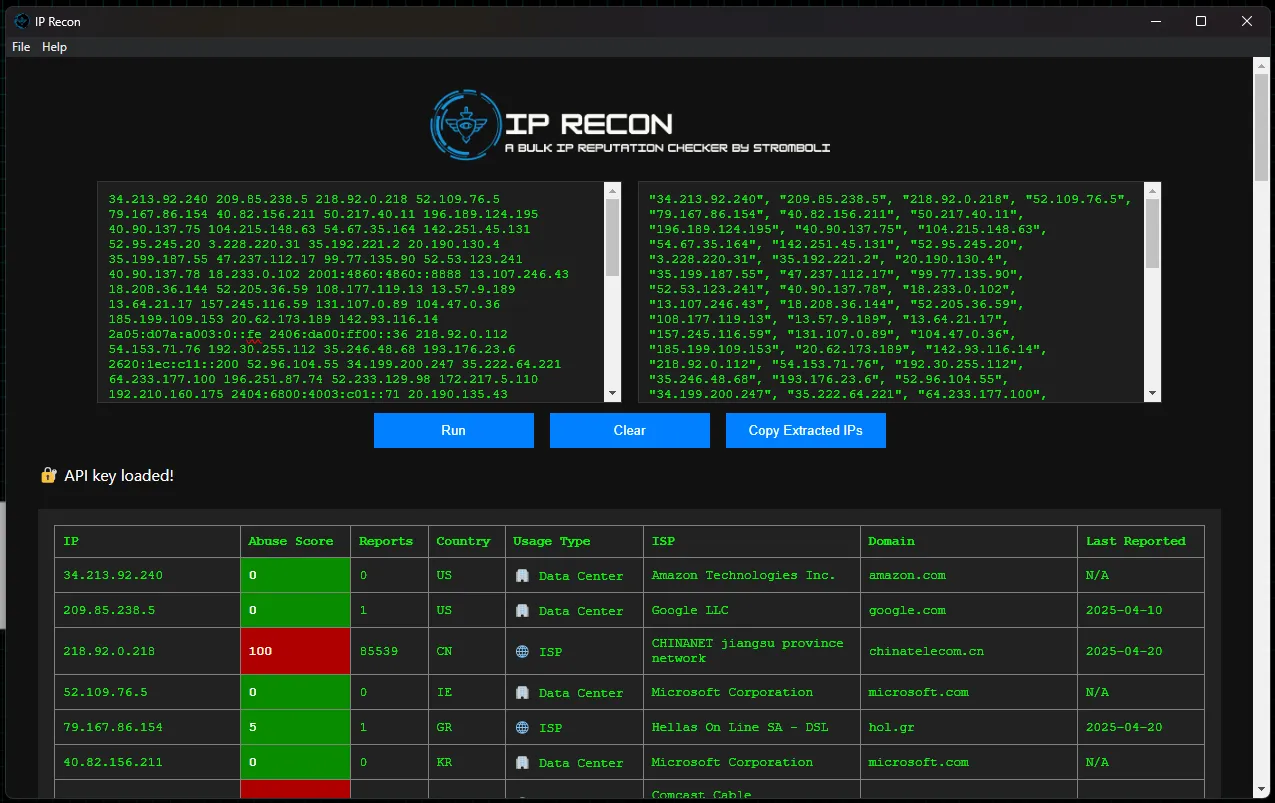
The program formats the list in a way that makes it easy to insert into KQL queries. Scanning the list, you notice it’s mostly expected traffic from Microsoft, AWS, and Google Cloud. However, further down the table, you begin to see some malicious IPs.
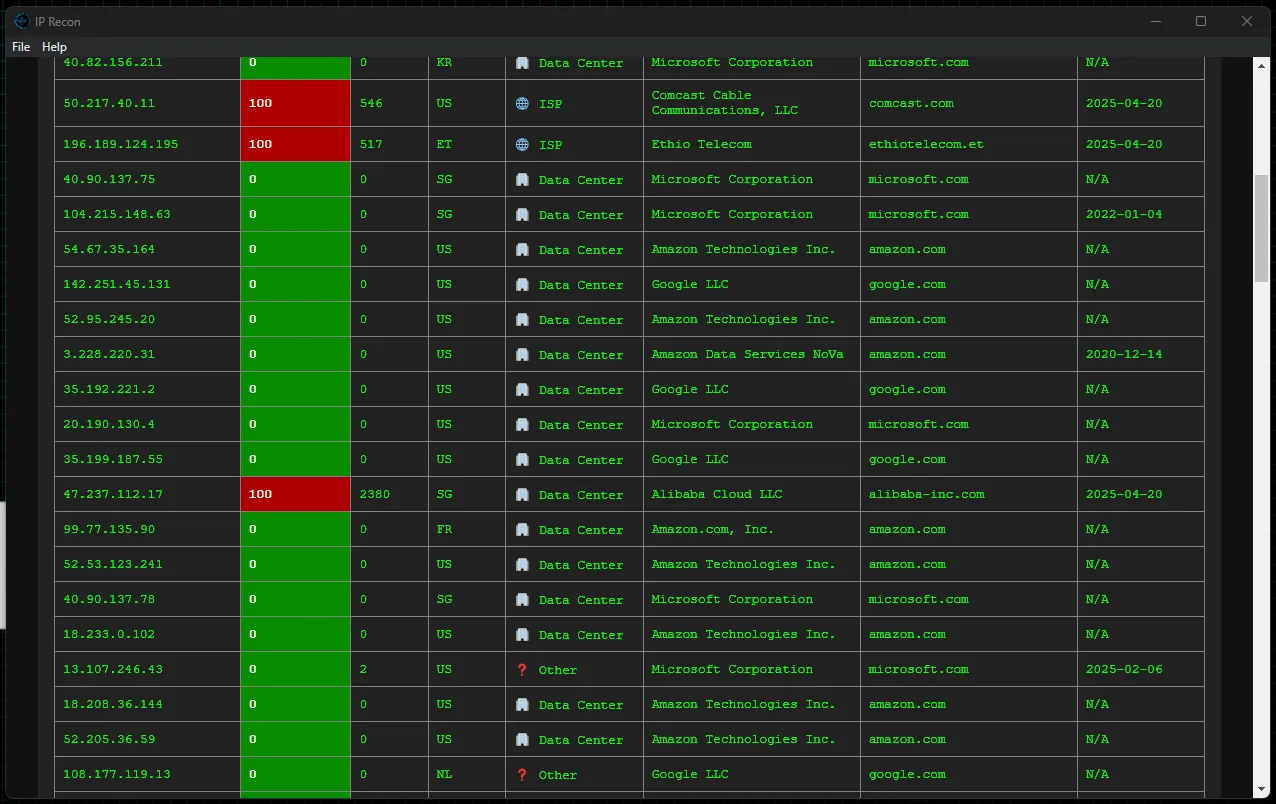
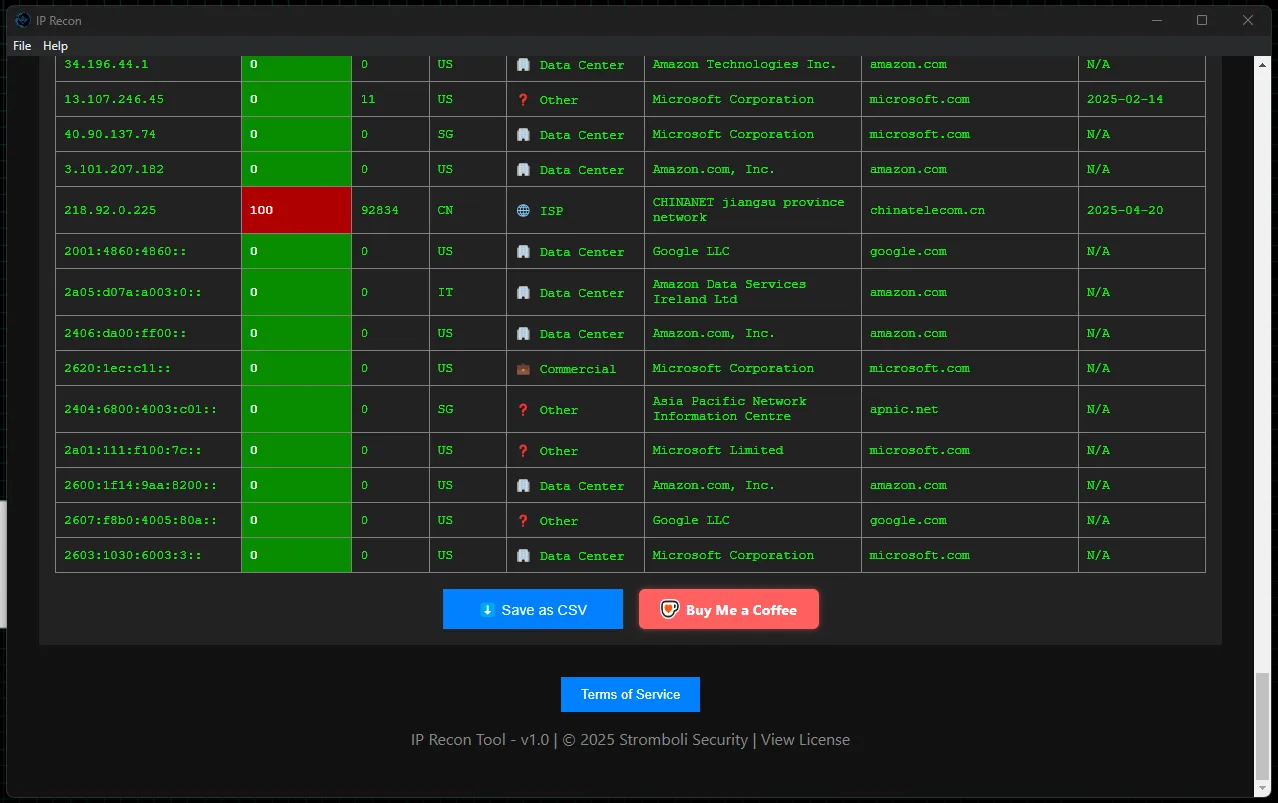
IP Recon allows you to quickly parse a list of IPs and identify possible threats for deeper investigation. Before I created this tool, I would download the CSV from the SIEM, ask an AI to format the list for another Python script, and wait. AI can be slow at this. IP Recon performs all the necessary steps for a bulk lookup in just three steps:
Copy the list in any format.
Paste the list into the input box.
Press the run button.
How Does IP Recon Accomplish This?
IP Recon accepts any arbitrary text. It extracts IPv4 and IPv6 addresses, removes duplicates, and filters out private IPs. Then, it formats the parsed data in a way that’s compatible with both KQL queries and AbuseIPDB API requests.
The tool gives the user a ready-to-use list for a KQL query like:
// Define your list of IPs
let TargetIPs = dynamic(["13.64.21.17","20.41.73.202","52.96.104.55","40.76.4.15","8.8.8.8"]);
// Search the CommonSecurityLog table for any matching IPs in Source or Destination fields
CommonSecurityLog
| where SourceIP in (TargetIPs) or DestinationIP in (TargetIPs)AbuseIPDB responds to the API call by providing reputation data on all submitted IPs. IP Recon then formats the results into a readable table and provides the option to download the data as a CSV file.
What is Required to Run IP Recon
IP Recon requires only one thing to get started: an AbuseIPDB API key. You can obtain a free key by registering an account. The free tier allows up to 1,000 IP lookups per day.
The user is prompted to enter the API key during the initial program run.
While IP Recon will soon be available in the Windows Store, the open-source Python version is already available on GitHub.
The repository includes complete installation instructions for running the application manually.
How Is My API Key Stored?
IP Recon uses Fernet AES encryption to securely store your API key. It does not require a password. Instead, Fernet encryption generates the encryption key using device-specific information—such as your MAC address or Windows GUID—combined with a salt.
This means that even if someone obtains your encrypted API key file, it won’t work on any other machine. The encryption is tightly bound to the original device.





