Improve Your Security Skills
Categories
IP Recon GitHub
Tags
aitm attack techniques cybersecurity Cybersecurity Getting Started Guides IP Address Reputation IP Recon kql KQL mfa microsoft sentinel Microsoft Sentinel Network Security Networking Nmap Penetration Testing phishing pyramid of pain security framework Security Tools session hijacking threat detection Threat Hunting Windows App Store
5 KQL Queries for Malicious Network Traffic
Hunt for threats in Microsoft Sentinel with these 5 KQL Queries for Malicious Network Traffic.
1832 words
|
9 minutes

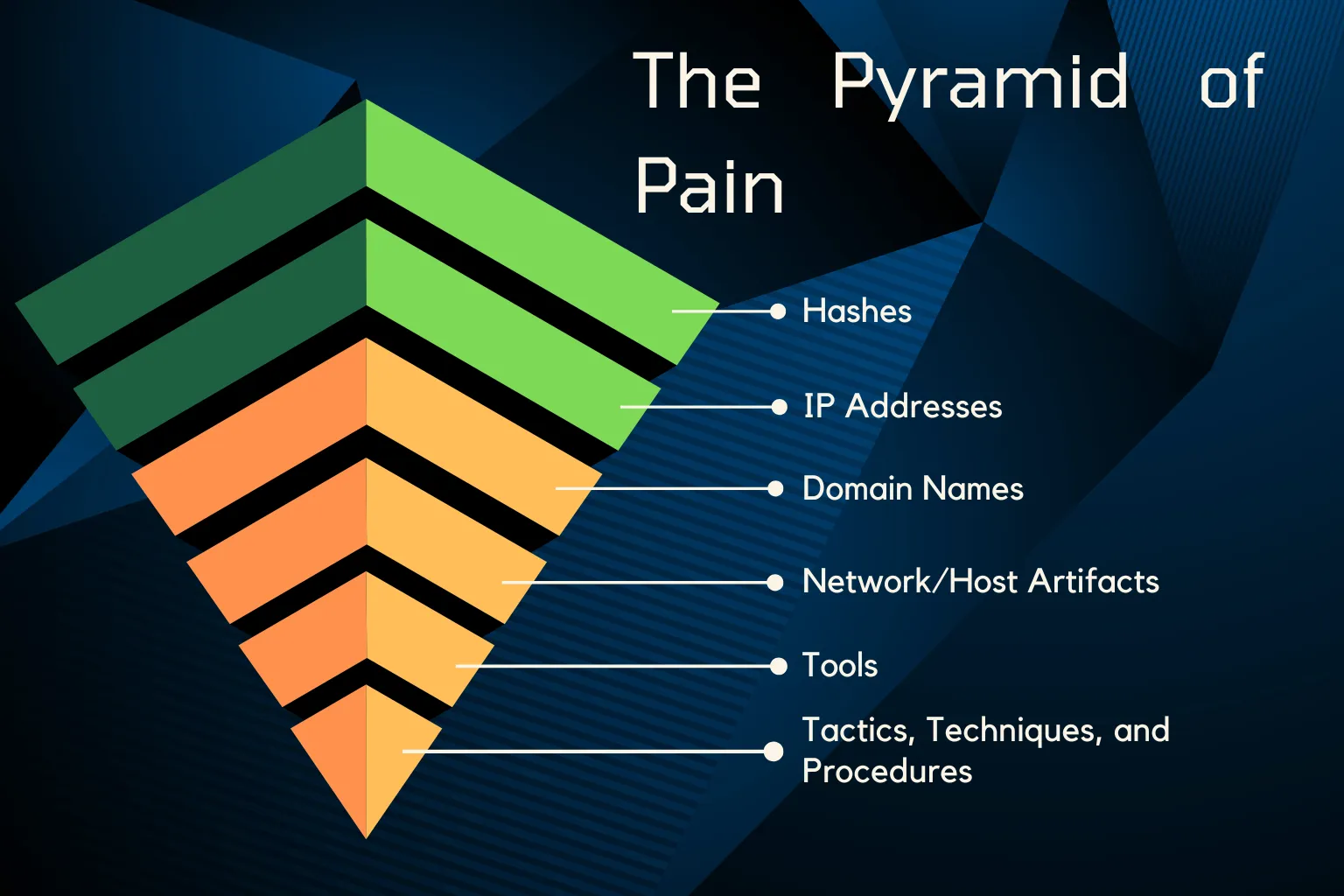
The Pyramid of Pain - A Guide to Cybersecurity Threat Detection
2025-05-07
Learn how the Pyramid of Pain framework helps prioritize cybersecurity defenses by understanding which threat indicators cause attackers the most difficulty when detected and blocked.
1835 words
|
9 minutes
AiTM Attacks Explained
A detailed guide explaining how Adversary-in-the-Middle (AiTM) attacks bypass MFA by hijacking session tokens, with detection techniques and threat hunting queries.
1702 words
|
9 minutes

Getting Started with IP Recon
2025-04-24
How to get started using the IP Recon Bulk Reputation Tool
358 words
|
2 minutes


Comprehensive Nmap Cheat Sheet
A detailed Nmap cheat sheet for mastering Nmap for security assessments and penetration testing.
554 words
|
3 minutes